Your data may be hiding your worst nightmares
RANSOM ATTACK
In 2022, organizations around the world detected nearly half a billion ransomware attacks (Statista, 2023), with almost half of them in American companies. The average ransom was over 1.5 million dollars (Sophos, 2023) and cost companies an additional 22 days of downtime. (Statista, 2021)
INSIDER THREAT
Attacks initiated by malicious insiders were the costliest, at an average of 4.9 million dollars withover 80% of breaches affecting data stored in the cloud. (Ponemon, 2022)
SOCIAL ENGINEERING
Almost 10% of breaches involved faking social accounts and accruing costs upward of 4.5 million dollars. Worse still, these attacks take an all time high of close to 300 days to detect and contain.(Ponemon, 2022)

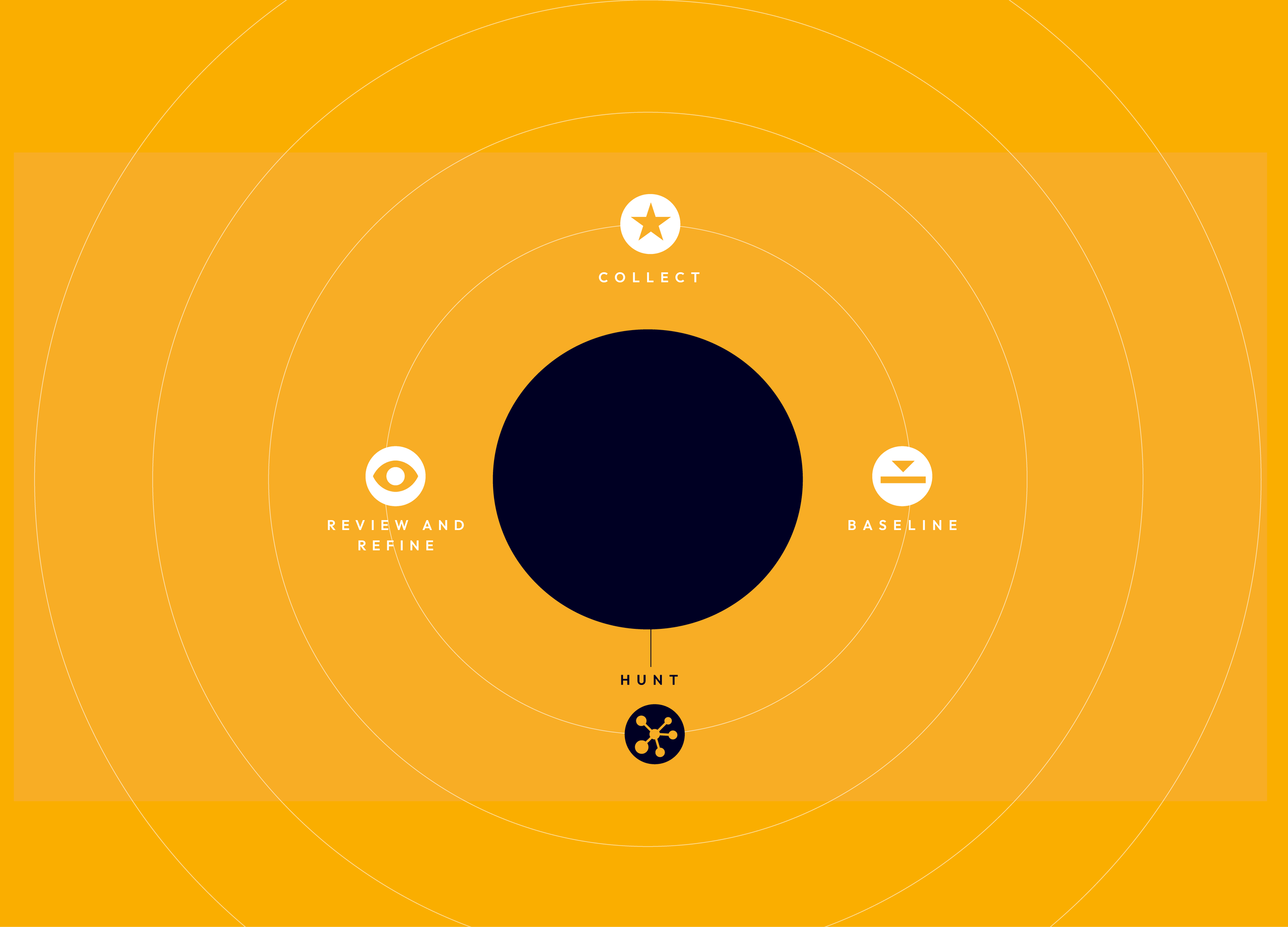
Your Ray of Light
QFunction does cybersecurity differently. By relying on scientific breakthroughs in AI and machine learning, QFunction works within your existing security stack to detect anomalies and threats within your data
QFunction partners with medium-size business owners and CISO’s to hunt for threats by focusing on anomalies in their existing data rather than trying to identify and label every type of threat individually. Instead of implementing yet another security tool in your environment, QFunction augments your existing security stack with AI/ML that let clients quickly sift through their noise and detect attacks before they even materialize
Q FUNCTION MAKES IT EASY TO DETECT, PREVENT, AND PROTECT
THREAT HUNTING
Find imminent threats that may have been lost in the noise of your data. Threat Hunting provides an independent, outside, analysis of your security data, looking for anomalies that could represent malicious intent.
TARGETED USER ENTITY BEHAVIOR ANALYTICS (UEBA)
UEBA lets you determine a ‘normal’ for select users or systems in your environment, which will allow you to easily detect any anomalies that deviate from that baseline. QFunction's UEBA targets high value users and/or systems exclusively, eliminating the need for a costly full blown UEBA solution that drains time, manpower, and tends to produce too much data and, consequently, too many false positives
SIEM SETUP AND CONSULTANCY
Work closely with me, a veteran of NASA’s JPL cyber security team, to set up your SIEM. Whether it spans a single department, a medium size business, or an entire division, I will show you which data you'll need to collect to maximize visibility of your data security.
The same principles used to safeguard cyber data can be appliled to any data set. I'll help you retrieve data from any source, identify, and score anomalies within the set and determine the appropriate action.
GENERAL ANOMALY DETECTION

EVERY DAY WITHOUT PROTECTION IS A POTENTIALLY COSTLY DAY.
GET A FREE EVALUATION OF YOUR CYBER SAFETY TODAY

HOW SAFE IS YOUR DATA?
ANSWER 4 QUESTIONS TO FIND OUT
1
2
3
4
YOUR ASSETS ARE MORE VALUABLE THAN YOU THINK.
YOUR DATA IS MORE VULNERABLE THAN YOU THINK.
I believe that your company is sitting on millions: your customer list, your phone numbers and email addresses, technical data you’ve amassed over the years, case studies, shipping addresses, inventory, strategies, IP, financial plans, bank accounts...
They may not look like much to you, but to an average cyber attacker they are pure gold.
MY ADVICE:
Don’t confuse a sense of security with real security.
Don’t underestimate the value of your assets to a bad actor.
Your data is more vulnerable than you think.
And your business is more valuable than you think.
Don’t be easy prey.
I can prove to you that AI and ML can protect your most valuable assets by detecting data anomalies linked to direct threats.